Sophos Firewall v22 - New features, hardening, and what to expect
Table of Contents
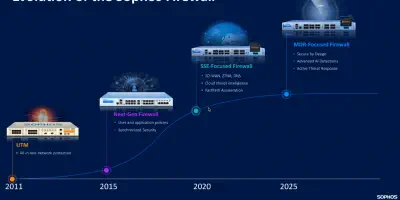
Sophos Firewall v22 (SFOS v22) is a major update that focuses on security hardening, improved visibility, and greater operational stability. The modernised Xstream architecture, hardened kernel, and new management features reduce the attack surface and simplify day-to-day administration. This article summarises the key innovations in SFOS v22, provides a critical assessment, and explains what they mean for Sophos admins.
Introduction
The early access phase for SFOS v22 began in October 2025, with the final version (GA) expected in early December. The goal of the release is clear: to make the firewall less vulnerable, easier to configure, and more robust in operation. The new version offers secure-by-design features, deeper telemetry, and many functions that have been requested for years.
Secure by design: hardening on multiple levels
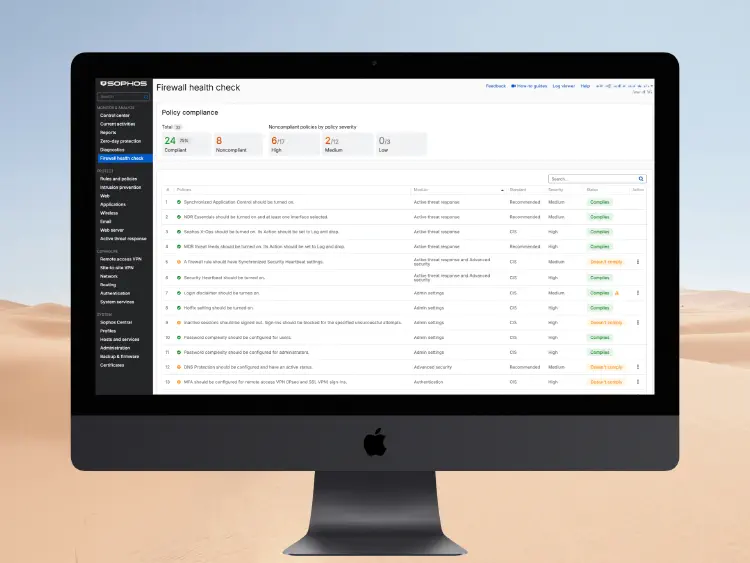
The new health check feature checks the firewall configuration against best practices and CIS benchmarks. It shows:
- Which settings are critical (e.g., MFA missing, WAN access open)
- Where exactly the error lies (including a link to the affected location)
- How to fix it
A widget in the dashboard shows the overall status, while the detailed view allows for targeted troubleshooting. Particularly helpful: the ratings of “High Risk,” “Medium Risk,” “Low Risk,” and “Pass” make prioritization easy.
The topic is so comprehensive that I have created a separate article here: Sophos Firewall v22 Health Check - Complete Overview
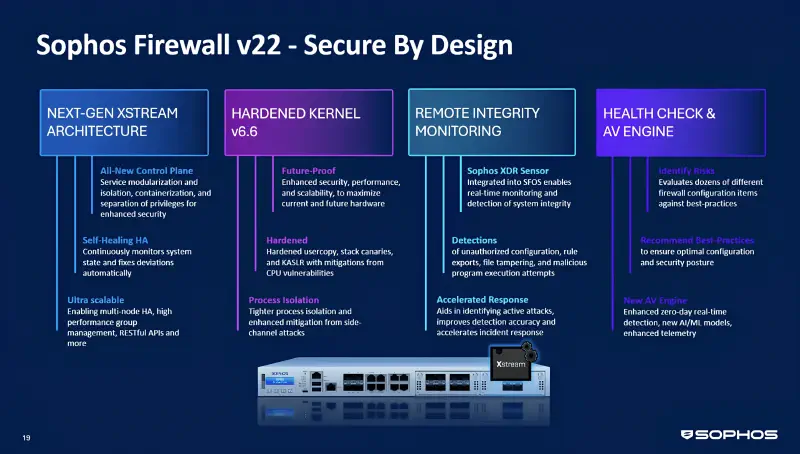
New Xstream architecture: modularity and self-healing
The control plane has been completely rebuilt:
- Services such as IPS and web filtering run in isolated containers
- A fault in one module no longer brings down the whole system
- HA clustering self-monitors and automatically corrects drift
- Foundation for future clustering and API integrations
- Early groundwork for on-demand firewall services (for example, scalable DPI services)
The architecture now aligns more closely with modern microservices principles, strictly separating functional units. Improved self-healing is especially relevant for HA environments: synchronisation issues, such as those caused by hung services in earlier versions, are detected and corrected automatically.
The result is greater stability, fewer failures, and a clear step towards a service-based firewall architecture.
Kernel 6.6+: more isolation and exploit protection
The upgrade to Linux kernel 6.6 delivers important security improvements:
- Protection against Spectre, Meltdown, L1TF, MDS, Retbleed, ZenBleed, Downfall
- Stack canaries, KASLR, usercopy hardening
- Extended namespaces for stronger separation of privileged processes
- Improved scalability on multi-core CPUs
The kernel is now on a par with modern Linux systems and offers better protection against low-level attacks. Deeper process isolation further improves resilience to side-channel attacks, which have recently put embedded systems back in the crosshairs.
Remote Integrity Monitoring: the firewall monitors itself
Another standout addition:
- The XDR sensor is now integrated into the firewall
- It detects rule exports, process starts, and file changes, among other events
- Alerts are sent to Sophos Central
- Also flags insider tampering and shell commands executed via the CLI
- Events include timestamp, user, and origin
A step towards host-based intrusion detection on the firewall itself. For audits or compliance reports, this data can be integrated into MDR or a SIEM. This provides visibility even into suspicious admin activity or operational policy drift.
Next-Gen Xstream Control Plane
- A new foundation for security and scalability: The control plane is modularised and strictly separates core services (IPS, Web, TLS). Each service runs in isolation, can be restarted independently, and minimises cross-process dependencies.
- Independent of hardware and environment: Optimised for modern multi-core CPUs. Behaviour and performance are consistent across hardware appliances, VMs, and cloud environments.
- Improved high availability with self-healing: In HA setups, the system monitors drift and synchronisation states and corrects them automatically, with a clear separation of data and control planes.
- Technical perspective and future: Preparation for n-node clustering, deeper containerisation, and full REST APIs for automation.
- Detection and response: improved threat intelligence: Broader, richer telemetry across services for faster triage.
- Threat feeds for NAT and WAF as well: Sophos threat feeds now also apply to DNAT and WAF rules. Malicious IPs are blocked on ingress to the firewall, whether for internal servers or user portals. This significantly reduces the attack surface.
ATR logging: less noise, clearer events
- Brute-force noise can be explicitly filtered
- Events are categorised by source (threat feed, NDR, MDR)
- Logs state clearly: ‘Attack detected, blocked, reason: XY’
- Logs now include NDR Essentials scores
Admins get context faster without switching between multiple platforms. This is particularly helpful during fast-moving incidents such as credential stuffing.
NDR Essentials: threat score in the log, region selectable
- NDR threat score now appears directly in logs
- Selectable analysis data centre (for example, EU)
- GDPR-aligned configuration options
This lowers the barrier to entry for smaller organisations that have so far avoided NDR due to data protection concerns.
Integration with XDR/MDR: more visibility
- Firewall integrity data flows into Sophos Central
- Correlates with endpoint and cloud telemetry
- Foundation for managed detection and response
- Early detection of lateral movement by attackers
This further embeds the firewall in the detection and response strategy, making it an active part of the defence.
Administration and monitoring: more convenience
- SNMP: CPU/NPU temperatures, PoE, and PSU can now be monitored, with an official MIB
- sFlow: up to five collectors, freely configurable sampling
- WebAdmin faster: page navigation no longer blocks the UI
- VPN interfaces: search and filter large numbers of XFRM interfaces
- API access: up to 64 allowed IPs/objects, configurable under ‘Administration’
- TLS 1.3: WebAdmin, VPN portal, and user portal now use modern encryption
- Instant Web Category Alerts: notifications when users access defined web categories (for example, in school environments)
- Better pagination: particularly for long lists (for example, firewall rules and objects)
API access control
Access to the management API can be restricted to IP addresses, ranges, or network objects (up to 64 entries). We recommend allowing only management networks, enabling logging, and reviewing access regularly.
Firmware updates via SSL with certificate pinning
Update endpoints are validated via SSL, including certificate pinning. In environments with strict egress policies, add the target FQDNs to allow lists.
HTTP/2 and TLS 1.3 for device access
WebAdmin, user, and VPN portals now support HTTP/2 and TLS 1.3 for faster handshakes and modern ciphers.
These are welcome improvements, especially for larger installations and MSP environments.
UTM-adjacent capabilities in SFOS
- WAF can now enforce MFA
- OTP via SHA-256/512
- Audit logs with before/after export (XML)
- Improved session management in the WAF (session ID handling via the firewall)
- Compatibility with existing OTP hardware tokens
Audit trail logs in detail
Phase 1 records changes to firewall rules, objects, and interfaces, including before/after values. Download via Diagnostics > Logs (configuration-audit.log). In future, this will be visible directly in the log viewer.
These enhancements matter for customers who want or need to migrate from UTM 9. The roadmap for SG UTM replacement solutions is further consolidated. With July 2026 fast approaching, v22 removes several of the remaining migration blockers.
Upgrade to SFOS v22: paths, duration, and notes
- EAP available, GA planned for December 2025
- The upgrade checks disk size and automatically expands the root partition if required (the first boot may therefore take longer)
- Typical paths: current v20/21 releases -> v22 directly; for older installations, first move to a supported MR if necessary
- Before every upgrade: take a backup, prepare the HA cluster properly, and plan a change window
- After the upgrade: run the health check and prioritise the findings
Important: backups are mandatory, especially for HA, SD-WAN, and multi-partition setups.
Personal impressions after 1 week
- Health check: Surfaces actionable findings quickly. In both setups it exposed weak defaults and forgotten legacy settings. Deep links to the affected location save time. Particularly helpful for firewall admins who do not configure firewalls regularly and want a clear checklist.
- Xstream architecture: Modules can be monitored independently and remain stable. In the HA lab, no manual intervention was needed for minor synchronisation issues.
- Logging/ATR/NDR: The additional context fields in the log simplify correlation with Central. NDR scores in the log are genuinely useful.
- SNMP/sFlow: The SNMP MIBs integrated seamlessly into existing monitoring with no special handling. sFlow provided sufficient visibility without the overhead of full PCAPs.
- Third-party threat feeds (NAT/WAF): Known malicious IPs are reliably blocked at the edge, including for port forwarding and WAF rules. In my lab, blocking works; however, hit logs are not yet appearing despite the option being enabled. I am awaiting EAP2 or GA and will retest.
Final words
SFOS v22 is not a cosmetic update but a deep architectural upgrade. The new Xstream foundation, the health check, and the API extensions make the firewall more robust and future-proof.
If you run a Sophos XGS today, you should look at v22. It is worth it for both security and day-to-day administration.
In the long term, Sophos is setting the course for a firewall architecture that can be operated in a containerised, integrity-assured, and automated fashion. That is the right direction at a time when firewalls need to do more than just block packets.
It is unfortunate that some long-standing weaknesses remain in such a major release. The GUI still feels sluggish in places, especially when switching between firewall rules, where load times are noticeable. In addition, columns in list views (for example, firewall or IPsec tables) still cannot be hidden individually, which hurts clarity. The log viewer also loses its filter settings on every restart, and NAT rules can neither be cloned nor grouped. Statistics or graphical stability indicators for IPsec connections are also missing.
In my view, these are items Sophos should address urgently in the next major update to improve the user experience and ease daily operations for administrators.
See you soon,
Joe