Sophos Firewall v22 Health Check - Complete Overview
Table of Contents
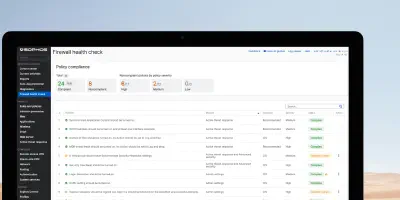
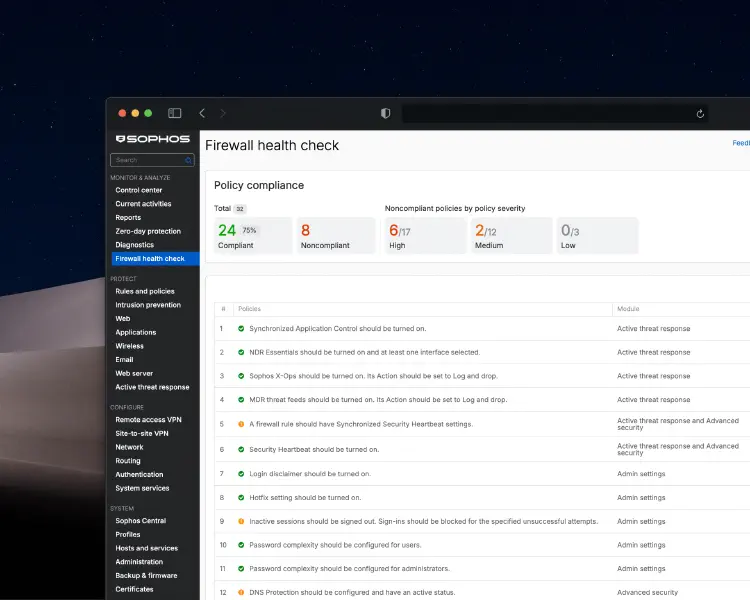
The new Firewall Health Check feature in Sophos Firewall v22 is an integrated configuration validation system that continuously assesses dozens of settings against the CIS Benchmarks and best practices. The checks are categorised by severity (High, Medium, Low) and organised by module (Active Threat Response, Admin Settings, Authentication, Device Access, etc.).
The following explains each Health Check policy, what it means, its severity, and a professional comment:
Active Threat Response
1. Synchronized Application Control should be enabled Severity: Medium | Standard: Recommended
Synchronized Application Control monitors all applications on connected endpoints via Security Heartbeat and automatically categorises and controls unknown applications. The firewall must be registered with Sophos Central, and this feature enabled, to gain full visibility of applications running on the network.
This capability is essential for modern network security because it unifies traditional network and endpoint security in a single architecture. In BYOD or fast-changing endpoint estates, it enables dynamic application control based on the real-time health of devices.
2. NDR Essentials should be enabled and at least one interface selected Severity: Medium | Standard: Recommended
NDR Essentials uses AI engines to analyse TLS-encrypted traffic and DNS requests without decryption to detect C2 communications and malicious activity. Enable it under Active Threat Response, select at least one internal interface, and configure a minimum threat score (recommended: 9-10).
NDR Essentials addresses a critical blind spot in encrypted environments where SSL/TLS inspection isn’t feasible due to privacy or performance constraints. AI-based behavioural analysis detects anomalies and suspicious communication patterns without deep packet inspection, which is particularly valuable against advanced persistent threats (APTs).
3. Sophos X-Ops should be enabled. Its Action should be set to Log and drop Severity: High | Standard: CIS
Sophos X-Ops Threat Feeds is a SophosLabs-managed global threat database of regularly updated IP addresses, domains, and URLs for C2 servers. The feature should be enabled and set to ‘Log and drop’ so the firewall automatically blocks traffic to known threats.
Integrating Sophos X-Ops threat intelligence delivers significant value with minimal configuration. Automatic threat feed updates ensure protection against the latest known threats and dramatically reduce the time to respond to zero-day exploits. The ‘Log and drop’ setting provides an optimal balance between security and visibility.
4. MDR threat feeds should be enabled. Its Action should be set to Log and drop Severity: High | Standard: Recommended
MDR Threat Feeds enables the Sophos MDR team to send real-time threat intelligence directly to the firewall based on analysis of telemetry data from the customer’s network. It requires a MDR licence and should be set to ‘Log and drop’ to automatically respond to active threats.
For organisations using the Sophos MDR service, this feature is indispensable, providing a direct operational link between the 24/7 SOC team and the firewall. Automated threat response drastically shortens dwell time and enables proactive defence before damage occurs.
Active Threat Response & Advanced Security
5. A firewall rule should enforce Synchronized Security Heartbeat Severity: Medium | Standard: CIS
Security Heartbeat enables communication between the firewall and Sophos-managed endpoints via Sophos Central to exchange threat and health status. Firewall rules can enforce access policies based on endpoint status (Green, Yellow, Red) to automatically isolate compromised devices.
Security Heartbeat is the core of the Sophos Synchronized Security architecture and enables dynamic decisions based on current threat status. Automatic isolation of compromised endpoints is particularly valuable, effectively preventing attackers’ lateral movement.
6. Security Heartbeat should be enabled Severity: High | Standard: CIS
Enable Security Heartbeat under System > Sophos Central by registering the firewall with Sophos Central. It requires a Network Protection licence and facilitates automatic status exchange between endpoints and the firewall every 15 seconds via port 8347.
Enabling Security Heartbeat is a foundational architectural decision that raises the security level of the entire estate. Without it, the firewall and endpoints act in isolation and critical context for security decisions is missing.
Admin Settings
7. Login disclaimer should be enabled Severity: Medium | Standard: CIS
A login disclaimer is a legal notice displayed on every sign-in to WebAdmin, the User Portal, or the CLI, requiring acknowledgement. It reduces the risk of inadvertent access by unauthorised users and supports legal action by removing ignorance as a defence.
Although technically simple, the login disclaimer is an important legal safeguard that is often pivotal in compliance audits and forensic investigations. In regulated industries (GDPR, HIPAA, PCI-DSS), a documented notice of system usage and monitoring is frequently a compliance requirement.
8. Automatic hotfix installation should be enabled Severity: High | Standard: CIS
Hotfixes are out-of-band security updates that can be installed automatically without downtime. Enable automatic installation under System > Backup & Firmware > Firmware > Hotfix to keep the firewall protected against known vulnerabilities and the network safe from exploits.
Automatic hotfix installation is a critical control that minimises the window between a vulnerability being disclosed and remediated. Since many attacks target known but unpatched vulnerabilities, this feature significantly reduces the risk of successful exploits.
9. Inactive sessions should auto-sign out. Sign-ins should be blocked after the specified number of unsuccessful attempts Severity: High | Standard: CIS
This setting enforces automatic sign-out after inactivity (recommended: maximum 10 minutes) and lockout after failed sign-in attempts. An unattended computer with an open admin session can allow unauthorised access; configure this under Administration > Admin and user settings > Login security.
Session management is a fundamental requirement that protects against privilege escalation and credential stuffing. The combination of timeout and account lockout implements defence-in-depth and minimises the exposure time of privileged access.
10. Password complexity should be configured for users Severity: High | Standard: CIS
Password complexity increases entropy and significantly impedes brute-force attacks. Require at least 12 characters, including upper and lower case letters, numbers, and special characters; configure under Administration > Admin and user settings > User password complexity settings.
Strong password policies are the first line of defence against credential-based attacks, which, according to the Verizon DBIR, remain among the most common attack vectors. Well-designed complexity rules balance security and usability and reduce the risk of weak, easily guessed passwords.
11. Password complexity should be configured for administrators Severity: High | Standard: CIS
Administrator password complexity should be stricter than for regular users because these accounts have extensive privileges. Require at least 14-16 characters across all character classes; configure under Administration > Admin and user settings > Administrator password complexity settings.
Privileged accounts are prime targets because they provide full system access. Increased complexity requirements for admin accounts reflect the heightened risk and should ideally be combined with regular rotation and MFA.
Advanced Security
12. DNS Protection should be configured and have an active status Severity: Medium | Standard: Recommended
DNS Protection is a cloud-based DNS service with integrated policy controls that blocks malicious domains and is managed in Sophos Central. The firewall must be registered as a location in Central, have the DNS Protection IP addresses configured as DNS servers, and appropriate policies assigned.
DNS is often the first stage of an attack when malware contacts C2 servers or data exfiltration occurs. DNS Protection provides preventive control at the DNS layer and complements other safeguards by detecting and blocking malicious domains before a connection is established.
Authentication
13. MFA should be configured for remote access VPN (IPsec and SSL VPN) sign-ins Severity: High | Standard: CIS
Multi-factor authentication (MFA) adds an extra security layer by requiring a time-based OTP (TOTP) from an authenticator app in addition to username and password. Configure under Authentication > Multi-factor authentication and select the VPN services.
VPN access is an exposed attack surface that provides direct access to the internal network. MFA isn’t optional here but essential, as compromised VPN credentials are one of the most common entry points for ransomware groups. Implementing MFA reduces the risk of successful credential-based attacks by over 99%.
14. MFA should be configured for WebAdmin Console and VPN Portal sign-ins Severity: High | Standard: CIS
Multi-factor authentication should also be enabled for the WebAdmin Console and VPN Portal to secure administrative access. Configure under Authentication > Multi-factor authentication by selecting ‘Web admin console’ and ‘User portal’.
Administrative interfaces are high-value targets because they provide full control over the security infrastructure. MFA for admin access is a critical control that prevents a single compromised credential set from escalating into a full security breach.
15. The firewall’s connections to authentication servers should be encrypted Severity: Medium | Standard: CIS
Connections to authentication servers (e.g. Active Directory, RADIUS, LDAP) should be encrypted to prevent man-in-the-middle attacks. When configuring external authentication servers, enable SSL/TLS or LDAPS to protect credentials in transit.
Unencrypted authentication protocols such as LDAP or RADIUS without TLS send credentials in plaintext or with weak encryption, making them susceptible to network sniffing. Encrypting these connections is especially critical in environments with multiple VLANs or sites.
Authentication Servers
16. Backups should be scheduled Severity: Low | Standard: CIS
Regular automated backups (daily, weekly, or monthly) should be configured to enable rapid recovery in an emergency. Configure under Backup & Firmware > Backup & Restore and store backups locally, via FTP, email, or Sophos Central; ensure backups are encrypted.
Backups are the last line of defence against ransomware, hardware failures, or misconfigurations. An automated strategy with offsite storage (e.g. Sophos Central) and encryption ensures business continuity and significantly reduces recovery time objectives (RTO).
Device Access
17. Public key authentication should be enabled for SSH access to the firewall Severity: High | Standard: Recommended
Public key authentication for SSH significantly improves security compared with password authentication and reduces brute-force risk. Generate an RSA or ED25519 key pair and add the public key under Administration > Device Access > Public Key Authentication.
SSH access with passwords is a known risk frequently compromised through automated brute-force attacks. Public key authentication virtually eliminates this risk and should be combined with disabling password authentication for maximum security.
18. User portal should not be accessible from WAN Severity: High | Standard: Recommended
Allowing WAN access to the User Portal significantly increases attack risk. Sophos strongly recommends permitting access only via LAN, VPN, or specific IP allowlists using Local Service ACL Exception Rules, never from 0.0.0.0/Any.
Exposing management interfaces to the internet is one of the most common misconfigurations and a prime target for automated attacks. Access should be limited to encrypted VPN connections or trusted IP ranges to minimise the attack surface.
19. WebAdmin Console should not be accessible from WAN Severity: High | Standard: CIS
The WebAdmin Console should never be directly reachable from the internet. Restrict administrative access to LAN, VPN, or strictly limited IP ranges; configure under Administration > Device Access > Local Service ACL Exception.
Exposing the admin console to the internet is a critical risk that can lead to full system compromise. Numerous security incidents begin with attacks against exposed management interfaces. This setting isn’t negotiable and must be strictly enforced in every environment.
20. MFA should be configured for the default admin Severity: High | Standard: CIS
The default admin account should be protected with MFA because it has the highest privileges. Configure under Authentication > Multi-factor authentication by selecting the admin user and enabling the ‘Web admin console’ service.
The default admin is often a primary target for credential stuffing because the username is predictable. MFA adds a critical layer and should be mandatory for this highly privileged account, regardless of password strength.
Notification Settings
21. Notification emails should be configured for system and security events Severity: Low | Standard: CIS
Email notifications inform administrators of critical system and security events such as failed sign-ins, IPS detections, or HA status changes. Configure the mail server under Administration > Notification settings, and select the events to monitor under System Services > Notification list.
Proactive notifications are essential for timely incident response and can be the difference between a thwarted threat and a successful attack. A well-tuned notification strategy should prioritise critical events and minimise false positives to avoid alert fatigue.
Pattern Updates
22. Automatic updates should be enabled for pattern download and installation Severity: High | Standard: CIS
Pattern updates contain signatures for antivirus, IPS, application control, and web filtering and should be downloaded and installed automatically every 15 minutes. Set this under Backup & Firmware > Pattern updates > Pattern download/installation interval to stay protected against current threats.
The threat landscape evolves at high speed, with thousands of new malware variants daily. Automatic pattern updates ensure the firewall is protected within minutes of new signatures being released, minimising the window of vulnerability to newly discovered threats.
Rules and Policies
23. A Web policy should be selected in a firewall rule Severity: Medium | Standard: Recommended
Web policies define categories and actions for web filtering and should be enabled in firewall rules to block unwanted or malicious sites. In firewall rules, select an appropriate policy in the ‘Web Policy’ section to control HTTP/HTTPS traffic.
Web-based threats remain among the most common infection vectors, from drive-by downloads to phishing sites. An active web policy in firewall rules implements preventive control and significantly reduces the likelihood of users accessing compromised or malicious websites.
24. Zero-day protection should be selected in a firewall rule Severity: High | Standard: CIS
Zero-day protection uses SophosLabs Intelix sandboxing to analyse suspicious downloads in isolated environments to detect unknown threats. In firewall rules, enable ‘Use Zero-day Protection’ under Web Policy to automatically analyse suspicious files.
Traditional signature-based detection fails against zero-day threats and advanced malware. Cloud-based sandbox analysis provides behavioural detection and protects against unknown threats without impacting firewall performance. This is especially valuable against polymorphic malware and APTs.
25. Intrusion prevention should be enabled. An IPS policy should be selected in a firewall rule Severity: High | Standard: CIS
IPS (Intrusion Prevention System) detects and blocks network-based attacks, known vulnerabilities, and zero-day exploits in real time. Under Protect > Intrusion prevention, create an IPS policy and select it in firewall rules in the ‘Intrusion prevention’ section.
IPS is a fundamental protection layer that prevents network and application-layer attacks before they reach target systems. An active IPS policy with regularly updated signatures protects against a wide range of exploits, from SQL injection and buffer overflows to C2 communication.
26. An Application control policy should be selected in a firewall rule Severity: Medium | Standard: CIS
Application control enables granular control over applications in the network through categorisation and bandwidth management. In firewall rules, select an application control policy to block or prioritise unwanted applications.
Modern attacks often leverage legitimate applications for data exfiltration or C2 communication. Application control provides granular visibility and control over applications regardless of ports and protocols, which is particularly valuable for enforcing acceptable use policies and preventing shadow IT.
27. An SSL/TLS inspection rule should have Action set to Decrypt Severity: High | Standard: CIS
SSL/TLS inspection decrypts and inspects encrypted traffic to detect malware in HTTPS connections. Under Protect > Rules and Policies > SSL/TLS inspection rules, create rules with the Action set to ‘Decrypt’; clients require the firewall CA certificate in their trust store.
With over 90% of web traffic encrypted, SSL/TLS inspection is indispensable for effective threat prevention. Without decryption, antivirus, IPS, and web filtering can’t inspect encrypted traffic, leaving a major security gap. Data privacy concerns should be addressed via selective bypass rules for sensitive categories (banking, healthcare).
28. An Allow firewall rule should not have all network and service settings set to Any Severity: Medium | Standard: CIS
Firewall rules with Source, Destination, and Service set to ‘Any’ are overly permissive and unnecessarily increase risk. Every Allow rule should define specific networks, hosts, and services to uphold least privilege and minimise the attack surface.
‘Any-Any-Any’ rules negate the fundamental purpose of a firewall and are a frequent finding in security audits. Every rule should be configured as restrictively as possible under least privilege to hinder lateral movement during a compromise and limit the blast radius.
Sophos Central
29. Sophos Central reporting should be enabled Severity: Medium | Standard: Recommended
Integration with Sophos Central enables centralised reporting with comprehensive dashboards, trends, and historical analysis across all managed devices. It is enabled automatically when the firewall is registered in Sophos Central under System > Sophos Central.
Centralised reporting is essential for multi-site environments and provides aggregated security insights that isolated firewalls can’t offer. Cloud-based long-term storage of logs and reports supports compliance requirements and enables trend analysis to identify systemic security issues.
30. The firewall should send its backups to Sophos Central Severity: Medium | Standard: Recommended
Automatic backup synchronisation with Sophos Central ensures configuration backups are stored offsite and available in case of disaster. Enable this under System > Sophos Central > Central Management.
Offsite backups are a critical best practice for disaster recovery and protect against data loss from ransomware that targets local backups. Automatic synchronisation with Sophos Central ensures a current, protected configuration is always available.
31. The firewall should be registered for Sophos Central management. Sophos Central management should be enabled Severity: Medium | Standard: Recommended
Registering with Sophos Central enables central management, firmware updates, policy administration, and access to cloud-based features such as Security Heartbeat, NDR Essentials, and DNS Protection. Register under System > Sophos Central by entering your Central credentials.
Sophos Central management underpins modern, cloud-assisted security architectures and enables consistent policy enforcement across all sites. Centralised administration reduces configuration errors, simplifies compliance evidence, and accelerates response through unified visibility.
Time
32. NTP server should be configured Severity: Low | Standard: CIS
Synchronising with a reliable NTP server (e.g. pool.ntp.org, time.google.com) is critical for accurate timestamps in logs, correlation with other systems, and cryptographic functions such as certificates. Configure under Administration > Time by selecting the NTP server and time zone.
Precise time synchronisation is often underestimated but fundamental for security operations. Inconsistent timestamps complicate or prevent event correlation across systems, which is critical in incident response and forensic analysis. Many cryptographic protocols and certificates are time-sensitive and don’t function correctly when clocks drift.
Summary
The Firewall Health Check feature in SFOS v22 implements a structured, risk-based approach to configuration hardening. The 32 checks cover all critical security areas from Active Threat Response through Authentication to Sophos Central integration and align with established standards such as the CIS Benchmarks.
The severity classification (High/Medium/Low) enables prioritised remediation, with high-severity policies such as MFA, SSL/TLS inspection, IPS, and X-Ops Threat Feeds requiring immediate attention. Continuous monitoring of compliance status helps administrators maintain a consistent security posture and proactively identify misconfigurations.
Final words
The new Health Check in Sophos Firewall v22 is a clear step towards automated compliance and a secure-by-design posture. It provides transparency and helps prevent common misconfigurations, especially in larger environments with multiple administrators. Nevertheless, it remains an analysis tool, not a guarantee of security. If you rely on green ticks, it’s easy to overlook context-dependent risks, such as misprioritised rules or insufficiently tested TLS inspection policies. Used correctly, however, the Health Check is a powerful control that helps administrators spot security gaps early and remediate them in a structured way.
See you soon,
Joe